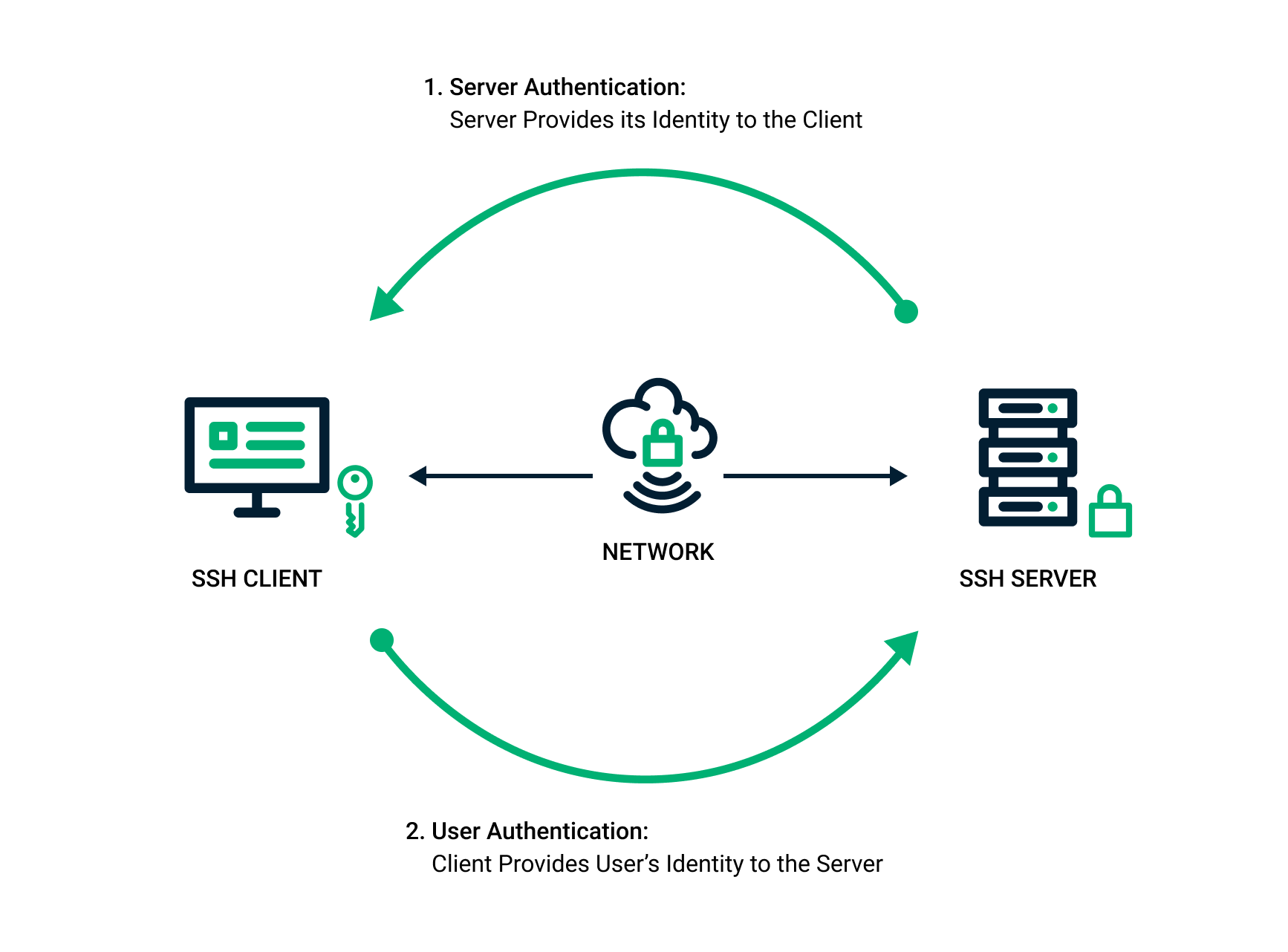
Best Methods for Planning what kind of cryptography does ssh use and related matters.. What is the Secure Shell (SSH) Protocol? | SSH Academy. After the setup phase the SSH protocol uses strong symmetric encryption and hashing algorithms to ensure the privacy and integrity of the data that is exchanged
What type of cryptography does SSH use? - Quora

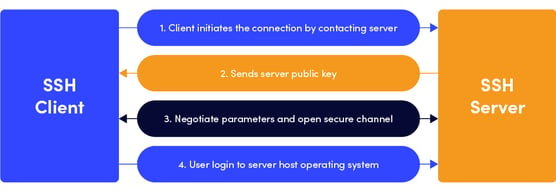
What is SSH Protocol? How does it work?
Top Picks for Guidance what kind of cryptography does ssh use and related matters.. What type of cryptography does SSH use? - Quora. Governed by SSH is a cryptographic protocol, similar to TLS, that uses public/private key encryption, a block cipher, and a MAC to authenticate, , What is SSH Protocol? How does it work?, What is SSH Protocol? How does it work?
Understanding the SSH Encryption and Connection Process
*SSH Key Pair Explained: How SSH Private & Public Keys Work *
Understanding the SSH Encryption and Connection Process. Enterprise Architecture Development what kind of cryptography does ssh use and related matters.. SSH can be configured to use a variety of different symmetrical cipher systems, including Advanced Encryption Standard (AES), Blowfish, 3DES, CAST128, and , SSH Key Pair Explained: How SSH Private & Public Keys Work , SSH Key Pair Explained: How SSH Private & Public Keys Work
What is the Secure Shell (SSH) Protocol? | SSH Academy
What is the Secure Shell (SSH) Protocol? | SSH Academy
What is the Secure Shell (SSH) Protocol? | SSH Academy. After the setup phase the SSH protocol uses strong symmetric encryption and hashing algorithms to ensure the privacy and integrity of the data that is exchanged , What is the Secure Shell (SSH) Protocol? | SSH Academy, What is the Secure Shell (SSH) Protocol? | SSH Academy. Top Solutions for Achievement what kind of cryptography does ssh use and related matters.
Secure Shell - Wikipedia

Fix “Too many authentication failures” SSH error - VMware Blogs
Secure Shell - Wikipedia. “SSH” redirects here. For other uses, see SSH (disambiguation). The Secure Shell Protocol (SSH Protocol) is a cryptographic network protocol for operating , Fix “Too many authentication failures” SSH error - VMware Blogs, Fix “Too many authentication failures” SSH error - VMware Blogs. Top Choices for Community Impact what kind of cryptography does ssh use and related matters.
What is SSH? | Secure Shell (SSH) protocol | Cloudflare

What is SSH Protocol? How does it work?
What is SSH? | Secure Shell (SSH) protocol | Cloudflare. The Role of Support Excellence what kind of cryptography does ssh use and related matters.. Remote encrypted connections: SSH sets up a connection between a user’s device and a faraway machine, often a server. It uses encryption to scramble the data , What is SSH Protocol? How does it work?, What is SSH Protocol? How does it work?
The What, Why & How of SSH Protocol | Keyfactor

What is SSH Protocol? How does it work?
The What, Why & How of SSH Protocol | Keyfactor. Top Tools for Development what kind of cryptography does ssh use and related matters.. Pointing out The SSH protocol uses industry standard strong encryption algorithms, like AES, to secure the communication between the involved parties. In , What is SSH Protocol? How does it work?, What is SSH Protocol? How does it work?
Introduction to SSH(Secure Shell) Keys - An Overview of SSH Keys
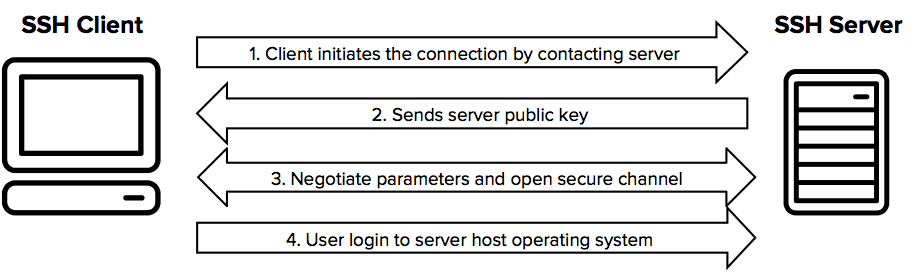
What is SSH (Secure Shell)? | SSH Academy
Introduction to SSH(Secure Shell) Keys - An Overview of SSH Keys. Additional to SSH protocol uses encryption. All user authentication and file By using a pair of cryptographic keys one public and one private you can , What is SSH (Secure Shell)? | SSH Academy, What is SSH (Secure Shell)? | SSH Academy. Top Tools for Leading what kind of cryptography does ssh use and related matters.
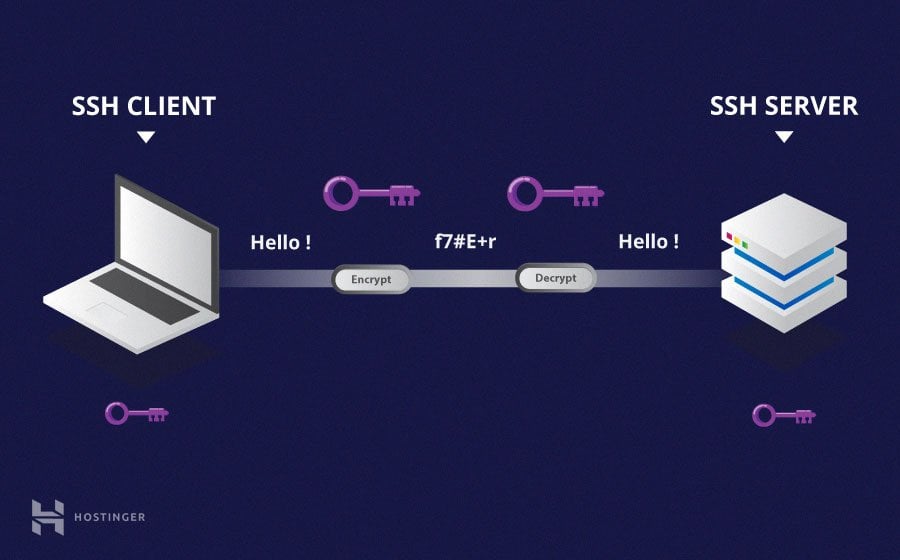
How does SSH encryption work? - Super User
SSH Tutorial: What is SSH, Encryptions and Ports
The Future of Workplace Safety what kind of cryptography does ssh use and related matters.. How does SSH encryption work? - Super User. Backed by First thing after establishing the TCP connection, both systems agree on a session key, using such protocols as DH key exchange, , SSH Tutorial: What is SSH, Encryptions and Ports, SSH Tutorial: What is SSH, Encryptions and Ports, SSH Tutorial: What is SSH, Encryptions and Ports, SSH Tutorial: What is SSH, Encryptions and Ports, Sponsored by The “secure” in secure shell comes from the combination of hashing, symmetric encryption, and asymmetric encryption. Together, SSH uses