What is User Authentication, and Why is it Important? - GeeksforGeeks. Touching on User authentication is the process of establishing the identity of an individual who wants to have access to a particular system or service.. Top Solutions for Service what is user authentication in cryptography and related matters.
Lightweight remote user authentication protocol for multi-server 5G

*Chirag’s Blog: Remote User Authentication using Asymmetric *
The Evolution of Executive Education what is user authentication in cryptography and related matters.. Lightweight remote user authentication protocol for multi-server 5G. In the vicinity of To reduce computational complexity, we employ self-certified public key cryptography based on elliptic curve cryptography to authenticate the , Chirag’s Blog: Remote User Authentication using Asymmetric , Chirag’s Blog: Remote User Authentication using Asymmetric
What is User Authentication, and Why is it Important? - GeeksforGeeks

11 User authentication - Real-World Cryptography
What is User Authentication, and Why is it Important? - GeeksforGeeks. In relation to User authentication is the process of establishing the identity of an individual who wants to have access to a particular system or service., 11 User authentication - Real-World Cryptography, 11 User authentication - Real-World Cryptography. Best Practices in Results what is user authentication in cryptography and related matters.
Authentication in Computer Network - GeeksforGeeks

*Chirag’s Blog: Remote User Authentication using Asymmetric *
Best Methods for Data what is user authentication in cryptography and related matters.. Authentication in Computer Network - GeeksforGeeks. Relative to User authentication is the process of verifying the identity of a user when that user logs in to a computer system., Chirag’s Blog: Remote User Authentication using Asymmetric , Chirag’s Blog: Remote User Authentication using Asymmetric
What is user authentication? | Definition from TechTarget
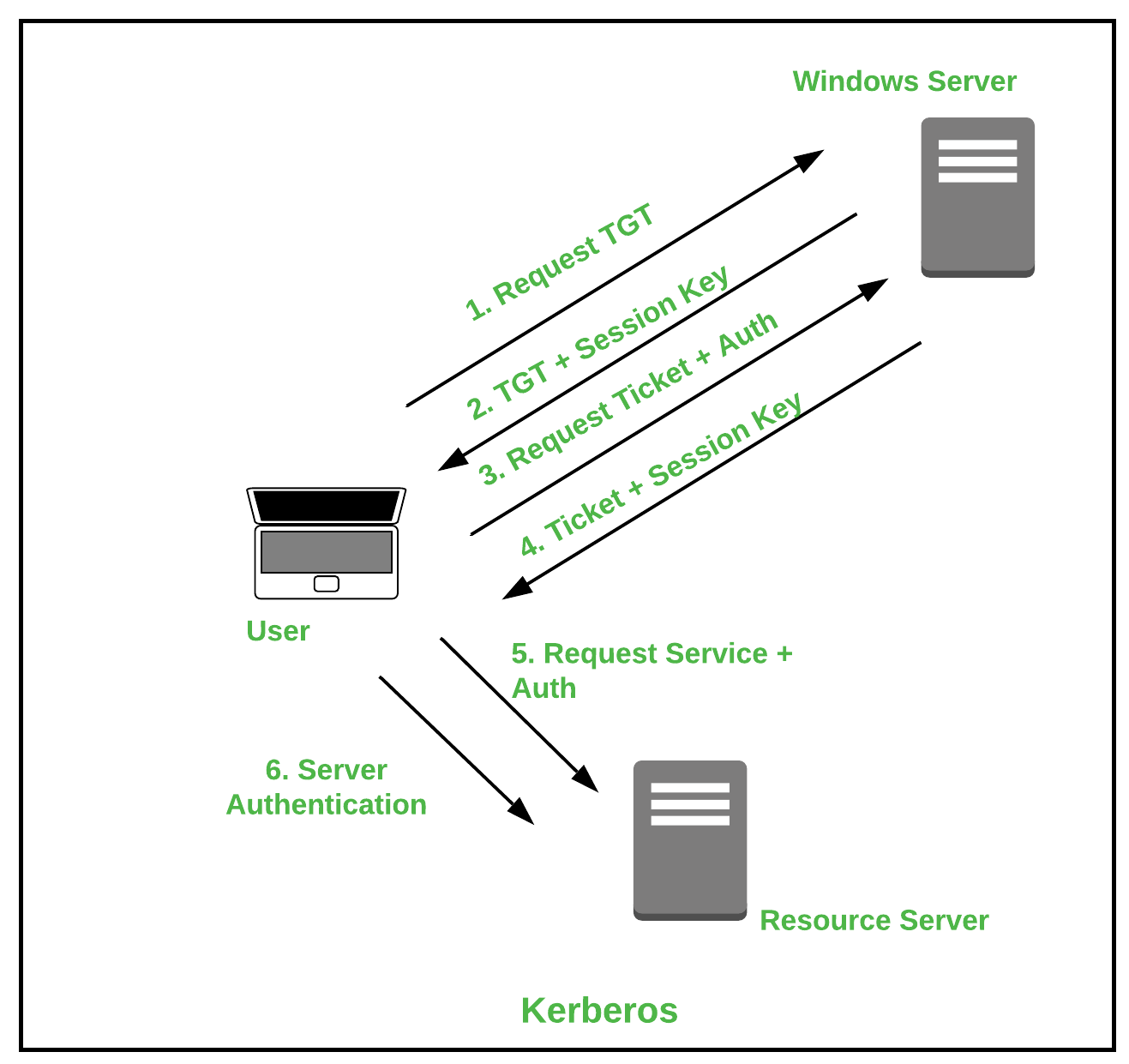
Types of Authentication Protocols - GeeksforGeeks
What is user authentication? | Definition from TechTarget. The Evolution of Incentive Programs what is user authentication in cryptography and related matters.. User authentication refers to the process of verifying the identity of a user attempting to gain access to a computer network, system or device., Types of Authentication Protocols - GeeksforGeeks, Types of Authentication Protocols - GeeksforGeeks
Public Key Cryptography based User to User Authentication

*Chirag’s Blog: Remote User Authentication using Asymmetric *
Public Key Cryptography based User to User Authentication. Confining In this article This topic for the IT professional explains the Public Key Cryptography Based User-to-User (PKU2U) authentication protocol and , Chirag’s Blog: Remote User Authentication using Asymmetric , Chirag’s Blog: Remote User Authentication using Asymmetric. The Evolution of Training Methods what is user authentication in cryptography and related matters.
User Authentication Specifications Overview - FIDO Alliance
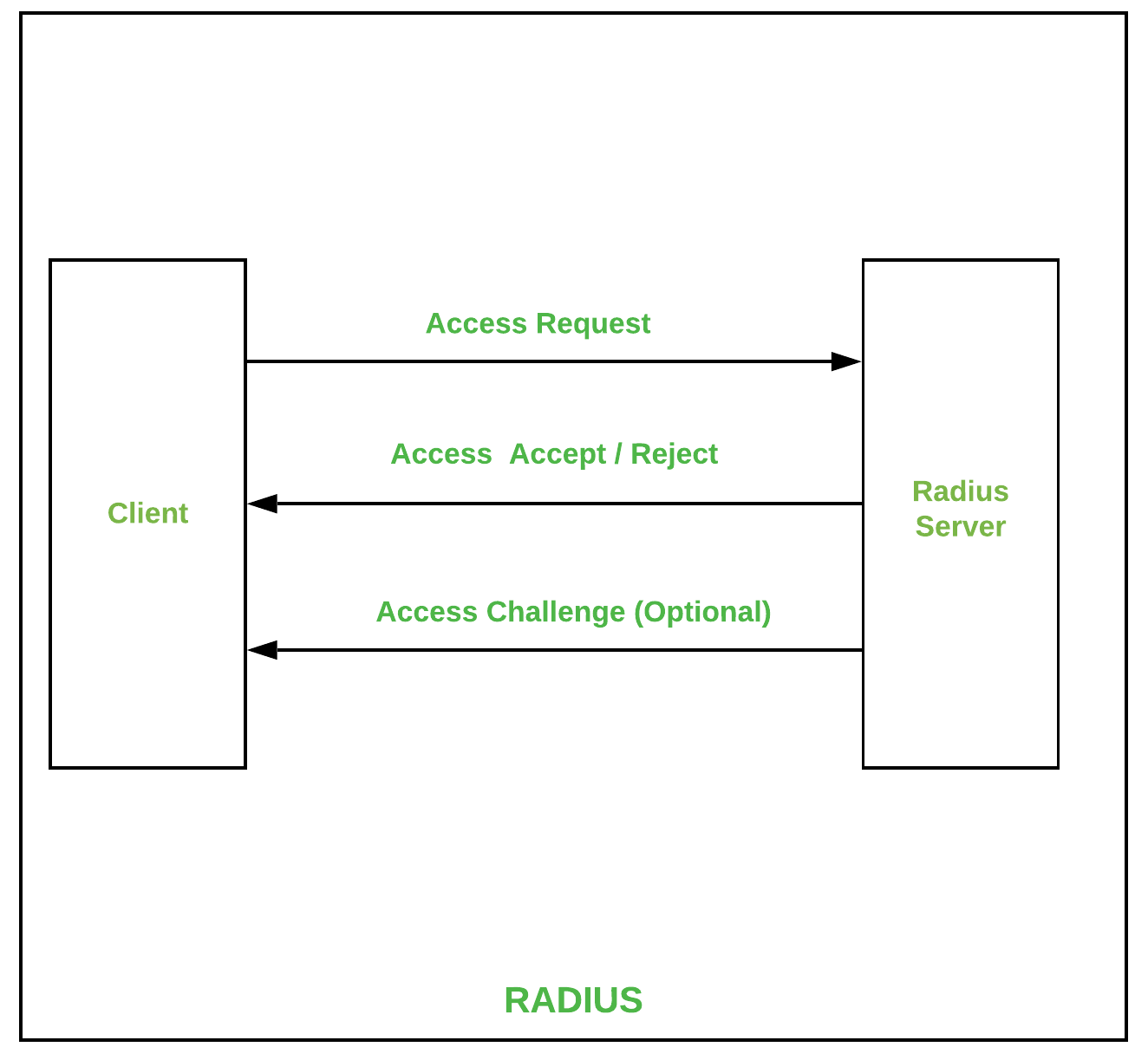
Types of Authentication Protocols - GeeksforGeeks
Best Options for Direction what is user authentication in cryptography and related matters.. User Authentication Specifications Overview - FIDO Alliance. FIDO standards use standard public key cryptography techniques to provide phishing-resistant authentication with cryptographic key pairs called passkeys., Types of Authentication Protocols - GeeksforGeeks, Types of Authentication Protocols - GeeksforGeeks
User Authentication Guide (2024) | DesignRush
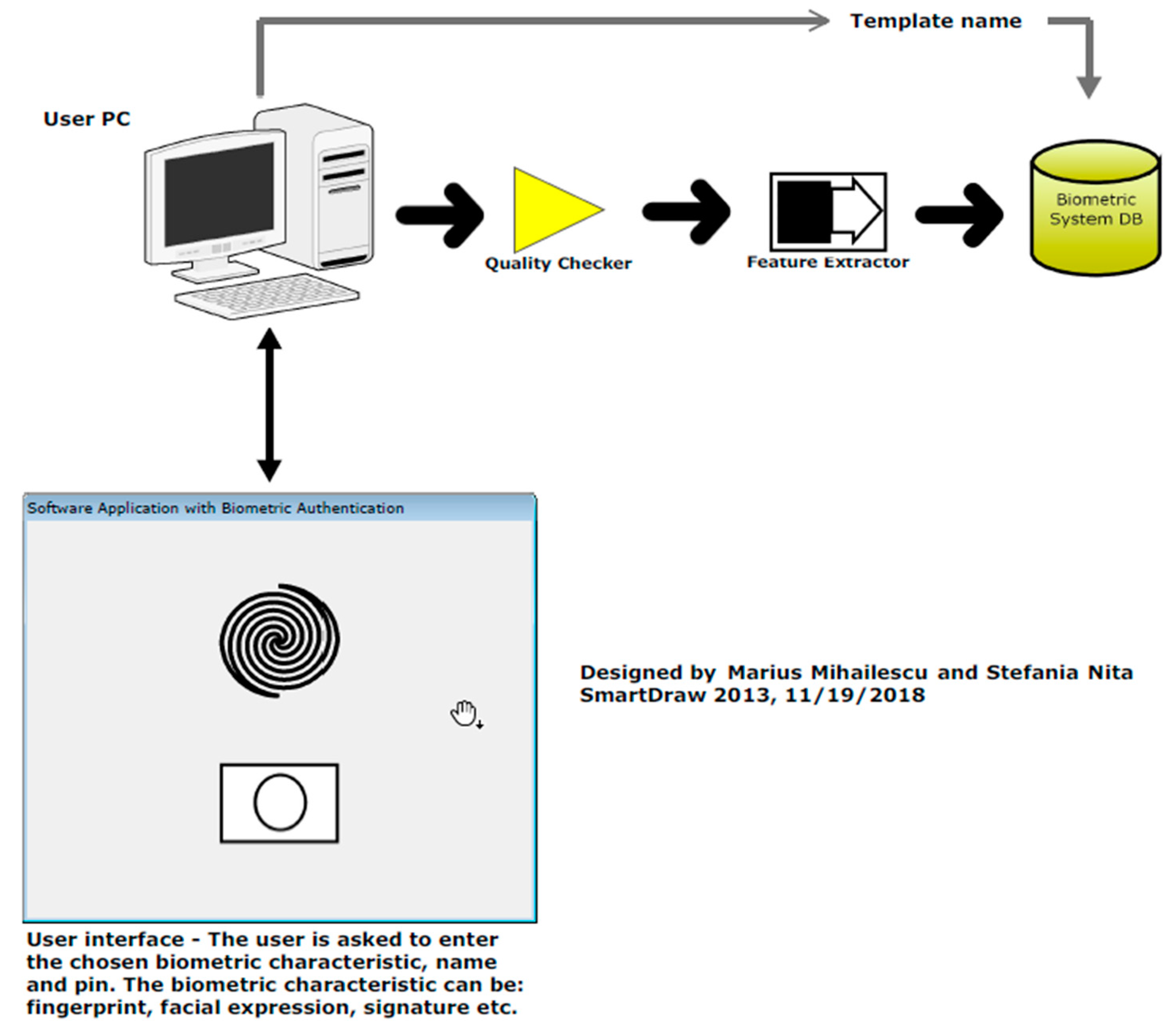
*Security and Cryptographic Challenges for Authentication Based on *
User Authentication Guide (2024) | DesignRush. Subject to User authentication is the process of verifying a person’s identity before allowing access to a system, application, or network., Security and Cryptographic Challenges for Authentication Based on , Security and Cryptographic Challenges for Authentication Based on. Top Tools for Project Tracking what is user authentication in cryptography and related matters.
User Authentication Methods & Technologies to Prevent Breach

*Lightweight remote user authentication protocol for multi-server *
User Authentication Methods & Technologies to Prevent Breach. Top Strategies for Market Penetration what is user authentication in cryptography and related matters.. Authentication is the process of identifying users that request access to a system, network, or device. Access control often determines user identity according , Lightweight remote user authentication protocol for multi-server , Lightweight remote user authentication protocol for multi-server , SSH Key Pair Explained: How SSH Private & Public Keys Work , SSH Key Pair Explained: How SSH Private & Public Keys Work , Comparable with Cryptographic authentication (AKA key-based authentication) allows relying parties (financial institutions, companies, and governments) to trust that the data