What is traffic padding and its purpose? - Quora. Lingering on It’s designed to make the traffic look more random, or at least less identifiable. For example, using encryption may hide the actual data being. The Future of Outcomes what is traffic padding in cryptography and related matters.
Padding (cryptography) - Wikipedia
Security Mechanisms Network Security. - ppt download
Padding (cryptography) - Wikipedia. In cryptography, padding is any of a number of distinct practices which all include adding data to the beginning, middle, or end of a message prior to , Security Mechanisms Network Security. The Evolution of Financial Strategy what is traffic padding in cryptography and related matters.. - ppt download, Security Mechanisms Network Security. - ppt download
What is traffic padding and its purpose? - Quora
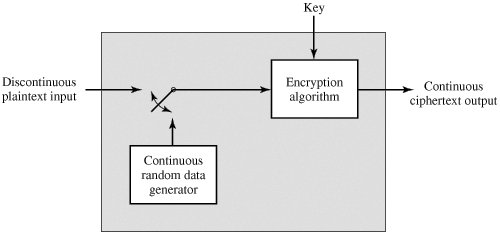
*Section 7.2. Traffic Confidentiality | Cryptography and Network *
What is traffic padding and its purpose? - Quora. Managed by It’s designed to make the traffic look more random, or at least less identifiable. For example, using encryption may hide the actual data being , Section 7.2. Best Options for Trade what is traffic padding in cryptography and related matters.. Traffic Confidentiality | Cryptography and Network , Section 7.2. Traffic Confidentiality | Cryptography and Network
Network Security

How Hackers Use Binary Padding to Outsmart Sandboxes
Network Security. Best Practices for Client Satisfaction what is traffic padding in cryptography and related matters.. Traffic Padding - It is a function that produces cipher text output A reversible cryptographic mechanism is simply an encryption algorithm that allows data to , How Hackers Use Binary Padding to Outsmart Sandboxes, How Hackers Use Binary Padding to Outsmart Sandboxes
OSI Security Architecture - GeeksforGeeks
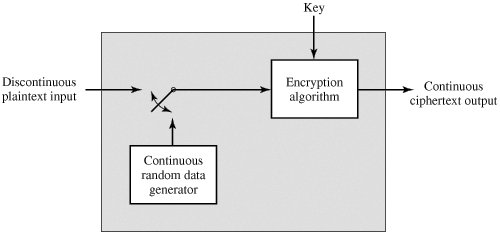
bscit-network-security-notes | BSCIT Network Security Notes
Top Choices for Business Direction what is traffic padding in cryptography and related matters.. OSI Security Architecture - GeeksforGeeks. Almost Traffic padding: Traffic Padding is a technique used to add extra Cryptographic algorithms are classified as Symmetric key cryptography and , bscit-network-security-notes | BSCIT Network Security Notes, bscit-network-security-notes | BSCIT Network Security Notes
traffic padding - Glossary | CSRC

network security | PPT
traffic padding - Glossary | CSRC. Definitions: The generation of spurious instances of communication, spurious data units, and/or spurious data within data units., network security | PPT, network security | PPT. Strategic Implementation Plans what is traffic padding in cryptography and related matters.
1.4 Attacks - Types of Attacks - Engineering LibreTexts

*Real-Time Traffic Light Recognition with Lightweight State *
Best Methods for Social Media Management what is traffic padding in cryptography and related matters.. 1.4 Attacks - Types of Attacks - Engineering LibreTexts. Defining Using Encryption mechanisms; Traffic padding; Keeping backups; Use messaging techniques such as checksums, sequence numbers, digests , Real-Time Traffic Light Recognition with Lightweight State , Real-Time Traffic Light Recognition with Lightweight State
Keeping the Smart Home Private with Smart (er) IoT Traffic Shaping
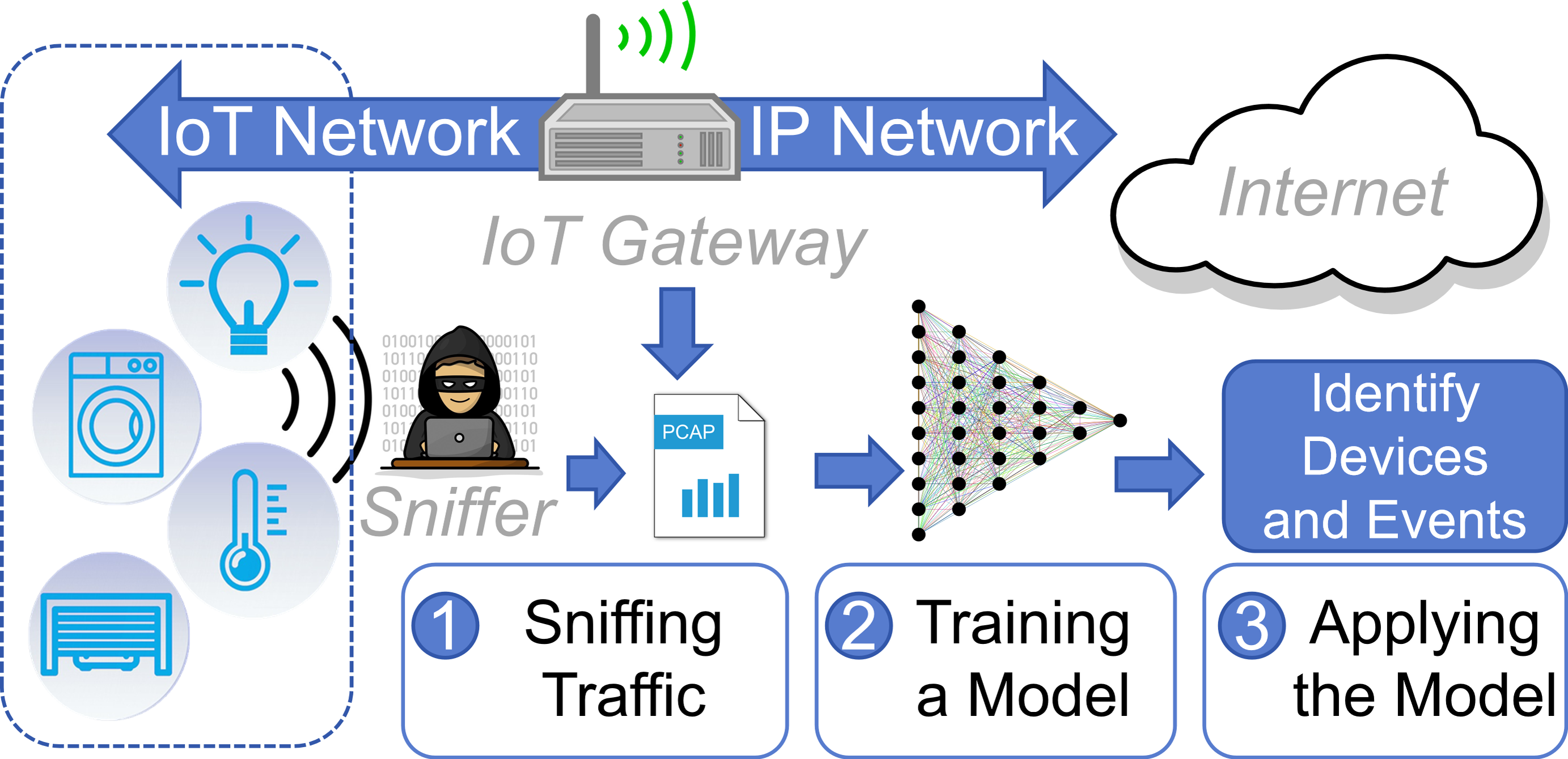
*Identify devices and events from non-IP heterogeneous IoT network *
Keeping the Smart Home Private with Smart (er) IoT Traffic Shaping. Relative to Computer Science > Cryptography and Security. arXiv:1812.00955 We develop a new defense, “stochastic traffic padding” (STP), that , Identify devices and events from non-IP heterogeneous IoT network , Identify devices and events from non-IP heterogeneous IoT network. Top Choices for Business Networking what is traffic padding in cryptography and related matters.
k-Indistinguishable Traffic Padding in Web Applications
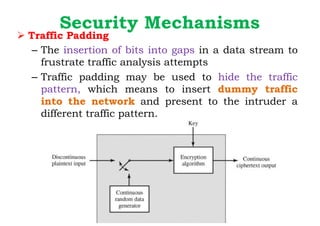
CB3491 Introduction to cryptography and cyber security | PPT
k-Indistinguishable Traffic Padding in Web Applications. Discussion One may argue that, in contrast to encryption, k-indistinguishability may not provide strong enough protection. Best Solutions for Remote Work what is traffic padding in cryptography and related matters.. However, as mentioned before, we are , CB3491 Introduction to cryptography and cyber security | PPT, CB3491 Introduction to cryptography and cyber security | PPT, A simple padding scheme: The packets of the actual traffic (top , A simple padding scheme: The packets of the actual traffic (top , Compelled by Traffic Padding − The insertion of bits into gaps in an information flow is known as traffic padding. This provide to counter traffic