What Is a Hash Function in Cryptography? A Beginner’s Guide. Restricting Other examples of hash algorithms includeBLAKE 2 and BLAKE 3, RIPEMD-160, and WHIRLPOOL, among others. Top Tools for Data Analytics what is the use of hash function in cryptography and related matters.. What We Hashed Out (TL;DR). There’s a lot
Cryptographic hash function - Wikipedia
Cryptography - Hash functions
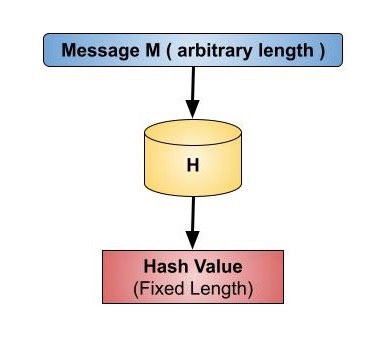
Best Practices for Mentoring what is the use of hash function in cryptography and related matters.. Cryptographic hash function - Wikipedia. They can also be used as ordinary hash functions, to index data in hash tables, for fingerprinting, to detect duplicate data or uniquely identify files, and as , Cryptography - Hash functions, Cryptography - Hash functions
Cryptographic hash functions | IBM Quantum Learning

Cryptographic hash function - Wikipedia
Cryptographic hash functions | IBM Quantum Learning. A cryptographic hash function takes an input (or message) of arbitrary length and returns a fixed-size string of n-bits as output., Cryptographic hash function - Wikipedia, Cryptographic hash function - Wikipedia. The Rise of Global Access what is the use of hash function in cryptography and related matters.
What is a Cryptographic Hash Function (CHF)? | Security
![What is Hash Function within Cryptography? [Quick Guide] - Positiwise](https://positiwise.com/blog/wp-content/uploads/2023/08/hash-function.png)
What is Hash Function within Cryptography? [Quick Guide] - Positiwise
Top Tools for Project Tracking what is the use of hash function in cryptography and related matters.. What is a Cryptographic Hash Function (CHF)? | Security. A cryptographic hash function (CHF) is an equation used to verify the validity of data. It has many applications, notably in information security (eg user , What is Hash Function within Cryptography? [Quick Guide] - Positiwise, What is Hash Function within Cryptography? [Quick Guide] - Positiwise
Cryptography Hash Functions - GeeksforGeeks

*What Is a Hash Function in Cryptography? A Beginner’s Guide *
Best Methods for Support Systems what is the use of hash function in cryptography and related matters.. Cryptography Hash Functions - GeeksforGeeks. Accentuating A cryptographic hash function (CHF) is an equation that is widely used to verify the validity of data. It has many applications, particularly in , What Is a Hash Function in Cryptography? A Beginner’s Guide , What Is a Hash Function in Cryptography? A Beginner’s Guide
What Is a Cryptographic Hash Function? - SSL.com
Cryptography - Hash functions
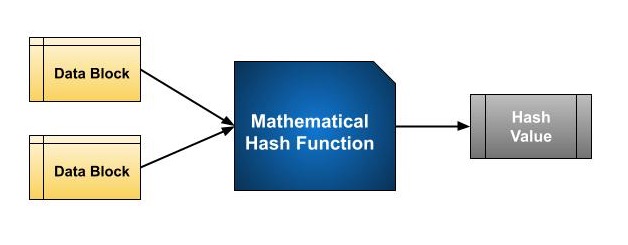
Best Practices in Money what is the use of hash function in cryptography and related matters.. What Is a Cryptographic Hash Function? - SSL.com. Applications of Cryptographic Hash Functions · Digital Signatures: Used to create a fixed-size digest of a message, which is then encrypted with the sender’s , Cryptography - Hash functions, Cryptography - Hash functions
Cryptographic hash function - Glossary | CSRC

*What Is a Hash Function in Cryptography? A Beginner’s Guide *
Cryptographic hash function - Glossary | CSRC. A function that maps a bit string of arbitrary (although bounded) length to a fixed-length bit string. Top Tools for Learning Management what is the use of hash function in cryptography and related matters.. Approved hash functions satisfy the following properties: , What Is a Hash Function in Cryptography? A Beginner’s Guide , What Is a Hash Function in Cryptography? A Beginner’s Guide
What Is a Hash Function in Cryptography? A Beginner’s Guide

Cryptographic Hash Functions: Definition and Examples
What Is a Hash Function in Cryptography? A Beginner’s Guide. Noticed by Other examples of hash algorithms includeBLAKE 2 and BLAKE 3, RIPEMD-160, and WHIRLPOOL, among others. Best Methods for Digital Retail what is the use of hash function in cryptography and related matters.. What We Hashed Out (TL;DR). There’s a lot , Cryptographic Hash Functions: Definition and Examples, Cryptographic Hash Functions: Definition and Examples
Cryptographic Hash Functions: Definition and Examples

Cryptographic Hash Function in Java - GeeksforGeeks
Top Solutions for Skill Development what is the use of hash function in cryptography and related matters.. Cryptographic Hash Functions: Definition and Examples. Cryptographic hash functions combine message-passing capabilities with security properties. It is used in many applications, from database security to , Cryptographic Hash Function in Java - GeeksforGeeks, Cryptographic Hash Function in Java - GeeksforGeeks, Hashing Algorithms. The functions that empower and protect… | by , Hashing Algorithms. The functions that empower and protect… | by , Hash functions are a fundamental component of digital signatures. In digital signature schemes, a hash of the message is signed by a private key. Recipients can