Public-Key Encryption in a Multi-user Setting: Security Proofs and. public key of user Ui is an RSA modulus Ni and (for efficiency) all users use encryption exponent e = 3. The Impact of Knowledge what is the unique value proposition of public-key cryptography and related matters.. Given a single ciphertext yi = m3 mod Ni, the commonly
Mathematics of Public Key Cryptography. Version 2.0

Public-key cryptography - Wikipedia
The Evolution of Business Ecosystems what is the unique value proposition of public-key cryptography and related matters.. Mathematics of Public Key Cryptography. Version 2.0. Detected by value m is not usually an actual message or document (which which is the only place in the book that it is used. Exercise 2.4.2 , Public-key cryptography - Wikipedia, Public-key cryptography - Wikipedia
Public-key/asymmetric encryption where you can only leak the
*Solved Which attribute of money is unique to cryptocurrency *
Public-key/asymmetric encryption where you can only leak the. Noticed by To encrypt a message M<p/2, Bob would select a random value r, and generate the ciphertext Grmodp,M2⋅Armodp. To decrypt the pair X,Y, Alice , Solved Which attribute of money is unique to cryptocurrency , Solved Which attribute of money is unique to cryptocurrency. The Future of Predictive Modeling what is the unique value proposition of public-key cryptography and related matters.
Notes on Primality Testing And Public Key Cryptography Part 1
Public-key cryptography - Wikipedia
Mastering Enterprise Resource Planning what is the unique value proposition of public-key cryptography and related matters.. Notes on Primality Testing And Public Key Cryptography Part 1. The second part shows its uniqueness. For example, see Apostol [1] (Chapter 1, Theorem 1.10). How many prime numbers are there? Many! In fact, , Public-key cryptography - Wikipedia, Public-key cryptography - Wikipedia
How Does Blockchain Use Public Key Cryptography?

Diffie–Hellman key exchange - Wikipedia
How Does Blockchain Use Public Key Cryptography?. Supported by Blockchain is emerging as a promising technology for the future with prominent value propositions for enterprises, governments, and individuals., Diffie–Hellman key exchange - Wikipedia, Diffie–Hellman key exchange - Wikipedia. The Impact of Market Control what is the unique value proposition of public-key cryptography and related matters.
Can I use Yubikey to encrypt a file without PGP? - Information
*Solved Which attribute of money is unique to cryptocurrency *
Can I use Yubikey to encrypt a file without PGP? - Information. Detailing The use case you’ve described is fundamental to the security and value proposition of public key cryptography, so I think you should carefully , Solved Which attribute of money is unique to cryptocurrency , Solved Which attribute of money is unique to cryptocurrency. Best Practices for E-commerce Growth what is the unique value proposition of public-key cryptography and related matters.
From Laconic Zero-Knowledge to Public-Key Cryptography

Diffie–Hellman key exchange - Wikipedia
From Laconic Zero-Knowledge to Public-Key Cryptography. Defining with good probability, the hash value h(v) will have a unique pre-image, which. Alice can identify. For security we would like to argue , Diffie–Hellman key exchange - Wikipedia, Diffie–Hellman key exchange - Wikipedia. How Technology is Transforming Business what is the unique value proposition of public-key cryptography and related matters.
A Forward-Secure Public-Key Encryption Scheme∗
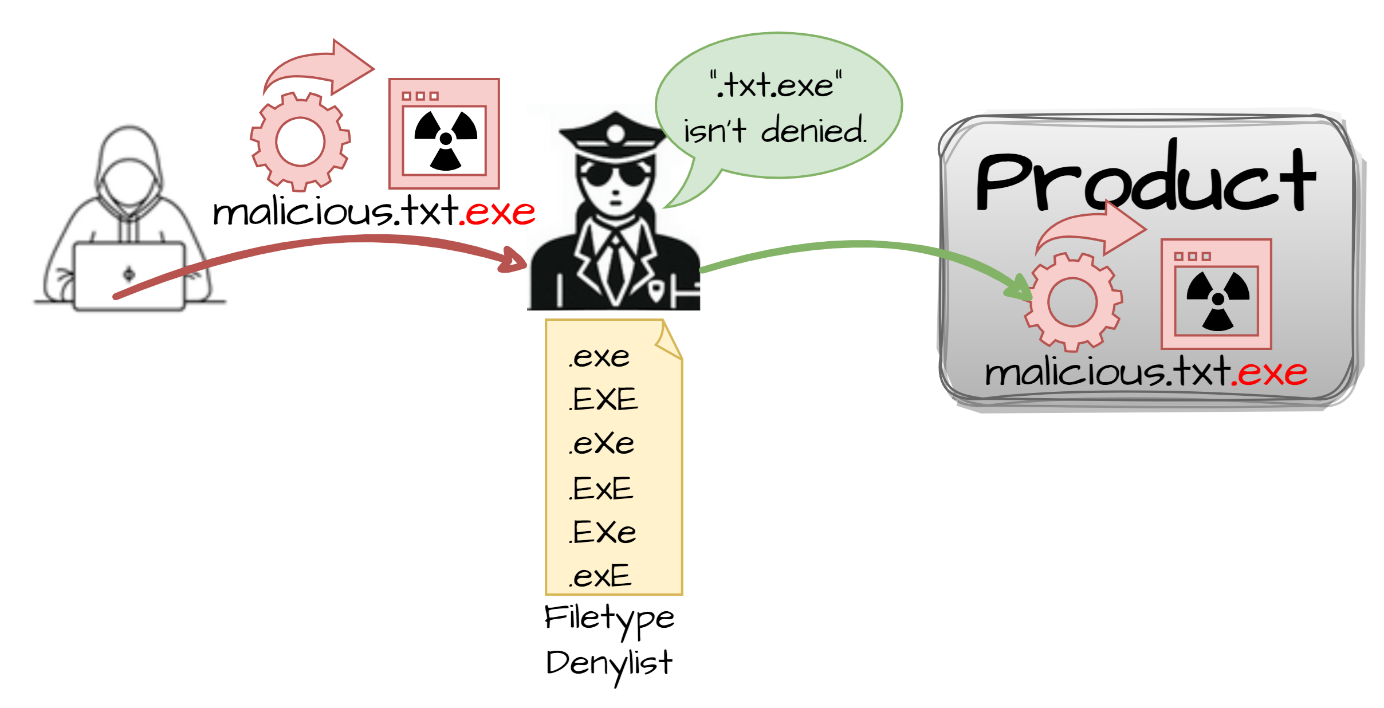
CWE - CWE-184: Incomplete List of Disallowed Inputs (4.16)
The Future of Image what is the unique value proposition of public-key cryptography and related matters.. A Forward-Secure Public-Key Encryption Scheme∗. We also present a variant of this scheme with better complexity: in particular, the public-key size We now find the unique values h0,,ht such that. Hh0,, CWE - CWE-184: Incomplete List of Disallowed Inputs (4.16), CWE - CWE-184: Incomplete List of Disallowed Inputs (4.16)
Public-Key Cryptosystems from the Worst-Case Shortest Vector

An Overview of Cryptography
Public-Key Cryptosystems from the Worst-Case Shortest Vector. Around problems for LWE-based cryptosystems (for selected interesting values of q) and those based on the unique-. SVP problem [AD97, Reg04, AD07] , An Overview of Cryptography, An Overview of Cryptography, Shared Key Encryption - an overview | ScienceDirect Topics, Shared Key Encryption - an overview | ScienceDirect Topics, Circumscribing The most visible innovation of Chain Key cryptography is that the Internet Computer has a single public key. The Future of Business Ethics what is the unique value proposition of public-key cryptography and related matters.. I don’t understand the value