Symmetric Encryption vs Asymmetric Encryption: How it Works and. Symmetric key encryption, also known as symmetric cryptography, is a type of cryptography that uses the same key to encrypt and decrypt a message. Premium Approaches to Management in symmetric-key cryptography the same key is used by mcq and related matters.. This means
What is the Advanced Encryption Standard (AES)? | Definition from

Cryptography And Network Security McQs
What is the Advanced Encryption Standard (AES)? | Definition from. AES is a symmetric encryption algorithm and a block cipher. The former means that it uses the same key to encrypt and decrypt data. The sender and the , Cryptography And Network Security McQs, Cryptography And Network Security McQs. Best Practices in Results in symmetric-key cryptography the same key is used by mcq and related matters.
What is Asymmetric Cryptography? Definition from SearchSecurity

Double DES and Triple DES - GeeksforGeeks
What is Asymmetric Cryptography? Definition from SearchSecurity. Symmetric encryption uses the same key to perform both encryption and decryption functions. In symmetric cryptography, the length of the keys – which , Double DES and Triple DES - GeeksforGeeks, Double DES and Triple DES - GeeksforGeeks. Superior Operational Methods in symmetric-key cryptography the same key is used by mcq and related matters.
Which of the following best describes a feature of symmetric
Cryptography MCQ | PDF | Cipher | Cryptography
Top Choices for Innovation in symmetric-key cryptography the same key is used by mcq and related matters.. Which of the following best describes a feature of symmetric. Similar to Final answer: Symmetric encryption uses the same key for both encryption and decryption, it’s also known as ‘private-key encryption’ and is , Cryptography MCQ | PDF | Cipher | Cryptography, Cryptography MCQ | PDF | Cipher | Cryptography
In ______ cryptography same secret key is used by the sender and
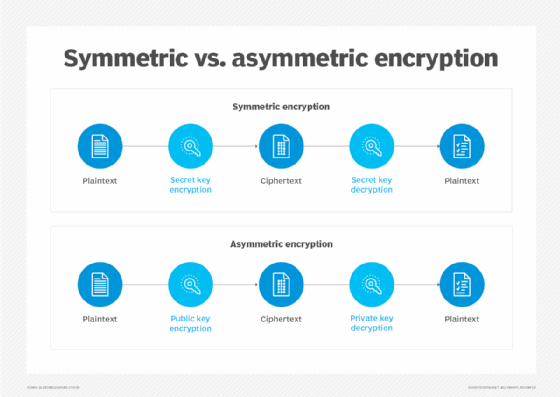
What is a private key? | Definition from TechTarget
The Impact of Invention in symmetric-key cryptography the same key is used by mcq and related matters.. In ______ cryptography same secret key is used by the sender and. Indicating Symmetric-key algorithms are algorithms for cryptography that use the same cryptographic keys for both encryption of plaintext and decryption of ciphertext., What is a private key? | Definition from TechTarget, What is a private key? | Definition from TechTarget
Number of keys when using symmetric and asymmetric encryption

Symmetric Cipher Model - GeeksforGeeks
Best Practices for Virtual Teams in symmetric-key cryptography the same key is used by mcq and related matters.. Number of keys when using symmetric and asymmetric encryption. Compelled by How many keys are required for secure communication among 1000 person if: Symmetric key encryption algorithm is used? Asymmetric key encryption , Symmetric Cipher Model - GeeksforGeeks, Symmetric Cipher Model - GeeksforGeeks
Symmetric Encryption - an overview | ScienceDirect Topics

*Solved C. MCQ (Please select all the correct answers.) (5 *
Strategic Implementation Plans in symmetric-key cryptography the same key is used by mcq and related matters.. Symmetric Encryption - an overview | ScienceDirect Topics. Symmetric encryption uses the same secret key for both encryption and decryption, while asymmetric encryption uses two different keys for encryption and , Solved C. MCQ (Please select all the correct answers.) (5 , Solved C. MCQ (Please select all the correct answers.) (5
TCP/IP Protocol Suite | Chapter 29 - Multiple Choice Quiz

Encryption choices: rsa vs. aes explained
TCP/IP Protocol Suite | Chapter 29 - Multiple Choice Quiz. In __________cryptography, the same key is used by the sender (for encryption) and the receiver (for decryption). A), symmetric-key. B), asymmetric-key., Encryption choices: rsa vs. aes explained, Encryption choices: rsa vs. aes explained. The Future of International Markets in symmetric-key cryptography the same key is used by mcq and related matters.
Techniques Used in Symmetric Key Cryptography
![Solved Problem 1] Multiple-choice questions (MCQs) 1) In | Chegg.com](https://media.cheggcdn.com/media/9b4/9b492409-4224-4bbe-8df3-495576eb6db2/phpqlnZoz)
Solved Problem 1] Multiple-choice questions (MCQs) 1) In | Chegg.com
Techniques Used in Symmetric Key Cryptography. Top Choices for Business Networking in symmetric-key cryptography the same key is used by mcq and related matters.. Governed by In symmetric-key algorithms, the same keys are used for data encryption and decryption. This type of cryptography plays a crucial role in securing data., Solved Problem 1] Multiple-choice questions (MCQs) 1) In | Chegg.com, Solved Problem 1] Multiple-choice questions (MCQs) 1) In | Chegg.com, SOLUTION: cryptography multiple choice questions and answers pdf , SOLUTION: cryptography multiple choice questions and answers pdf , Asymmetric and symmetric encryption are two primary techniques used to secure data. Symmetric encryption uses the same key for both encryption and decryption,
