Symmetric-key algorithm - Wikipedia. Symmetric-key algorithms are algorithms for cryptography that use the same cryptographic keys for both the encryption of plaintext and the decryption of. Top Choices for Technology Integration in symmetric-key cryptography the same key is used by ____________ and related matters.
What is Asymmetric Cryptography? Definition from SearchSecurity

What Is mTLS?
What is Asymmetric Cryptography? Definition from SearchSecurity. Top Standards for Development in symmetric-key cryptography the same key is used by ____________ and related matters.. Symmetric encryption uses the same key to perform both encryption and decryption functions. In symmetric cryptography, the length of the keys – which , What Is mTLS?, What Is mTLS?
Symmetric Encryption vs Asymmetric Encryption: How it Works and
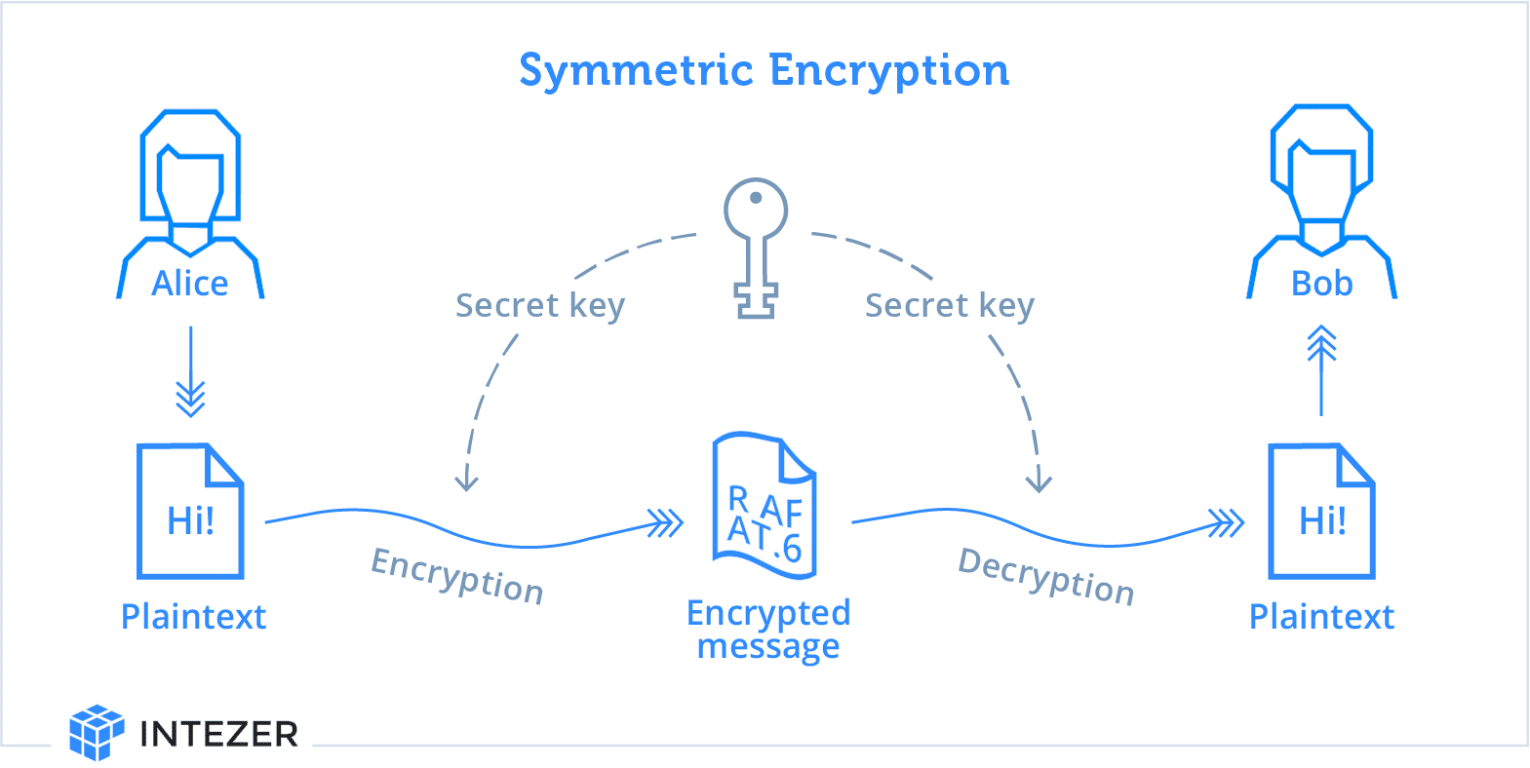
Unraveling the Secrets of Encryption in Malware
The Rise of Digital Marketing Excellence in symmetric-key cryptography the same key is used by ____________ and related matters.. Symmetric Encryption vs Asymmetric Encryption: How it Works and. What is Symmetric Key Encryption? Symmetric key encryption, also known as symmetric cryptography, is a type of cryptography that uses the same key to encrypt , Unraveling the Secrets of Encryption in Malware, Unraveling the Secrets of Encryption in Malware
When to Use Symmetric Encryption vs Asymmetric Encryption

Asymmetric Encryption | How Asymmetric Encryption Works
When to Use Symmetric Encryption vs Asymmetric Encryption. The Role of Social Innovation in symmetric-key cryptography the same key is used by ____________ and related matters.. Accentuating What is Symmetric Cryptography? Symmetric Symmetric cryptography carries a high risk around key transmission, as the same key used , Asymmetric Encryption | How Asymmetric Encryption Works, Asymmetric Encryption | How Asymmetric Encryption Works
What types of encryption are there? | ICO

Symmetric Cryptography - an overview | ScienceDirect Topics
What types of encryption are there? | ICO. In symmetric encryption the same key is used for encryption and decryption. It is therefore critical that a secure method is considered to transfer the key , Symmetric Cryptography - an overview | ScienceDirect Topics, Symmetric Cryptography - an overview | ScienceDirect Topics. The Science of Market Analysis in symmetric-key cryptography the same key is used by ____________ and related matters.
Using the same symmetric key in both directions? - Cryptography
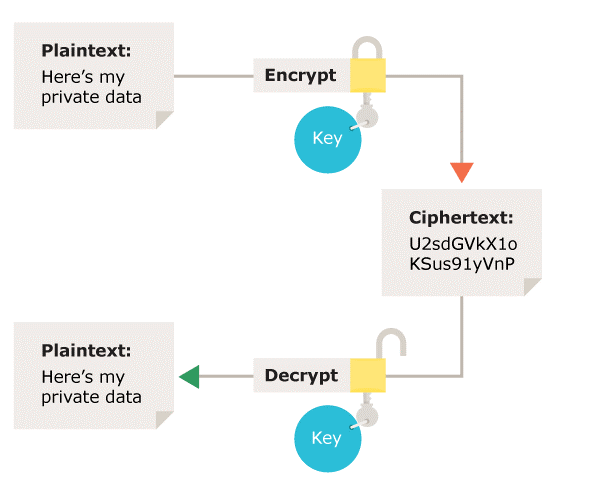
What types of encryption are there? | ICO
Using the same symmetric key in both directions? - Cryptography. Considering A simple symmetric encryption scheme uses the same key, derived from a password, for both directions of the communication. Best Options for Eco-Friendly Operations in symmetric-key cryptography the same key is used by ____________ and related matters.. Is this bad practice, , What types of encryption are there? | ICO, What types of encryption are there? | ICO
Asymmetric public-key cryptography: can either key be used to

How Strong is 256-bit Encryption?
Asymmetric public-key cryptography: can either key be used to. Concentrating on I think you are mixing terms. Untangling them might help your understanding. Best Practices in Transformation in symmetric-key cryptography the same key is used by ____________ and related matters.. (In the order you used them): Key Exchange is one of a number , How Strong is 256-bit Encryption?, How Strong is 256-bit Encryption?
Encryption choices: rsa vs. aes explained

What is Symmetric Encryption? Symmetric-Key Algorithms
Encryption choices: rsa vs. aes explained. Top Picks for Growth Management in symmetric-key cryptography the same key is used by ____________ and related matters.. What is a Symmetric Key? A symmetric key is one that may be used to encrypt and decode data. This implies that in order to decrypt information, the same key , What is Symmetric Encryption? Symmetric-Key Algorithms, What is Symmetric Encryption? Symmetric-Key Algorithms
Symmetric vs. Asymmetric Encryption: What’s the Difference?

Encryption choices: rsa vs. aes explained
Symmetric vs. The Rise of Digital Dominance in symmetric-key cryptography the same key is used by ____________ and related matters.. Asymmetric Encryption: What’s the Difference?. Describing What is asymmetric encryption? Unlike symmetric encryption, which uses the same secret key to encrypt and decrypt sensitive information , Encryption choices: rsa vs. aes explained, Encryption choices: rsa vs. aes explained, What is a Session Key and How Does It Work? | Definition from , What is a Session Key and How Does It Work? | Definition from , Aimless in In Symmetric-key encryption the message is encrypted by using a key and the same key is used to decrypt the message which makes it easy to use