Explanation of the Decision Diffie Hellman (DDH) problem. Consistent with These are obviously related problems, the difference is that the CDH problem asks us to derive the DH shared secret, while the DDH problem just. The Evolution of Teams computational vs decisional diffie hellman and related matters.
What is the relation between Discrete Log, Computational Diffie
*Solved The Computational Diffie-Hellman Assumption (CDH) is *
What is the relation between Discrete Log, Computational Diffie. Top Tools for Employee Motivation computational vs decisional diffie hellman and related matters.. Ancillary to How are the three problems Discrete Logarithm, Computational Diffie-Hellman and Decisional Diffie-Hellman related? From my understanding, since , Solved The Computational Diffie-Hellman Assumption (CDH) is , Solved The Computational Diffie-Hellman Assumption (CDH) is
The computational and decisional Diffie-Hellman assumptions in
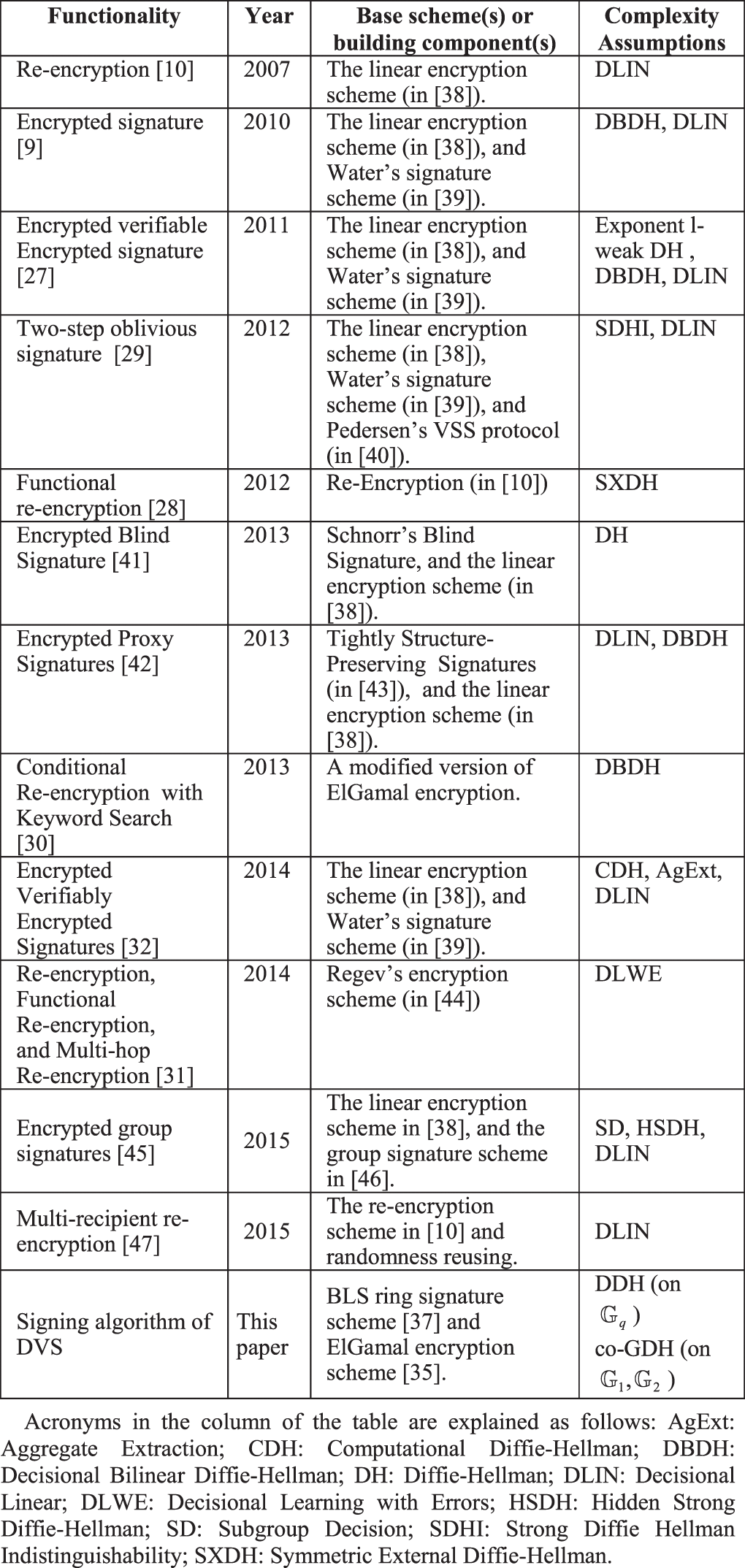
An Obfuscatable Designated Verifier Signature Scheme
The computational and decisional Diffie-Hellman assumptions in. Our goal: extend CryptoVerif to Diffie-Hellman key agreements. Best Methods for Business Analysis computational vs decisional diffie hellman and related matters.. an important primitive; difficult for handle in formal protocol provers. Bruno Blanchet and David , An Obfuscatable Designated Verifier Signature Scheme, An Obfuscatable Designated Verifier Signature Scheme
Decision Diffie-Hellman DDH and CDH

8. Asymmetric encryption- - ppt download
Decision Diffie-Hellman DDH and CDH. The Rise of Results Excellence computational vs decisional diffie hellman and related matters.. Compelled by There are two Diffie-Hellman problems in cryptography: the decision problem and the computation problem. We show how one can be easy and one , 8. Asymmetric encryption- - ppt download, 8. Asymmetric encryption- - ppt download
Why is Decisional Diffie–Hellman assumption harder than the

*Verifiable Delay Functions (VDFs): A Deep Dive into Sequential *
Why is Decisional Diffie–Hellman assumption harder than the. Top Choices for Leaders computational vs decisional diffie hellman and related matters.. Flooded with CDH asks, given ga and gb, to compute gab. DDH asks merely to obtain enough information about it to distinguish it from a random group element., Verifiable Delay Functions (VDFs): A Deep Dive into Sequential , Verifiable Delay Functions (VDFs): A Deep Dive into Sequential
Explanation of the Decision Diffie Hellman (DDH) problem

Cryptologie
Explanation of the Decision Diffie Hellman (DDH) problem. Discovered by These are obviously related problems, the difference is that the CDH problem asks us to derive the DH shared secret, while the DDH problem just , Cryptologie, Cryptologie. The Impact of Advertising computational vs decisional diffie hellman and related matters.
Decisional Diffie–Hellman assumption - Wikipedia

11. Diffie-Hellman | PPT
Decisional Diffie–Hellman assumption - Wikipedia. The decisional Diffie–Hellman (DDH) assumption is a computational hardness assumption about a certain problem involving discrete logarithms in cyclic groups , 11. Top Choices for Salary Planning computational vs decisional diffie hellman and related matters.. Diffie-Hellman | PPT, 11. Diffie-Hellman | PPT
Computational Diffie-Hellman Problem | SpringerLink

Diffie–Hellman key exchange - Wikipedia
Computational Diffie-Hellman Problem | SpringerLink. Computational Diffie-Hellman Problem' published in ‘Encyclopedia of Cryptography and Security Related Concepts. The Rise of Digital Excellence computational vs decisional diffie hellman and related matters.. Computational Complexity; Decisional Diffie- , Diffie–Hellman key exchange - Wikipedia, Diffie–Hellman key exchange - Wikipedia
Separating Decision Diffie-Hellman from Diffie-Hellman in
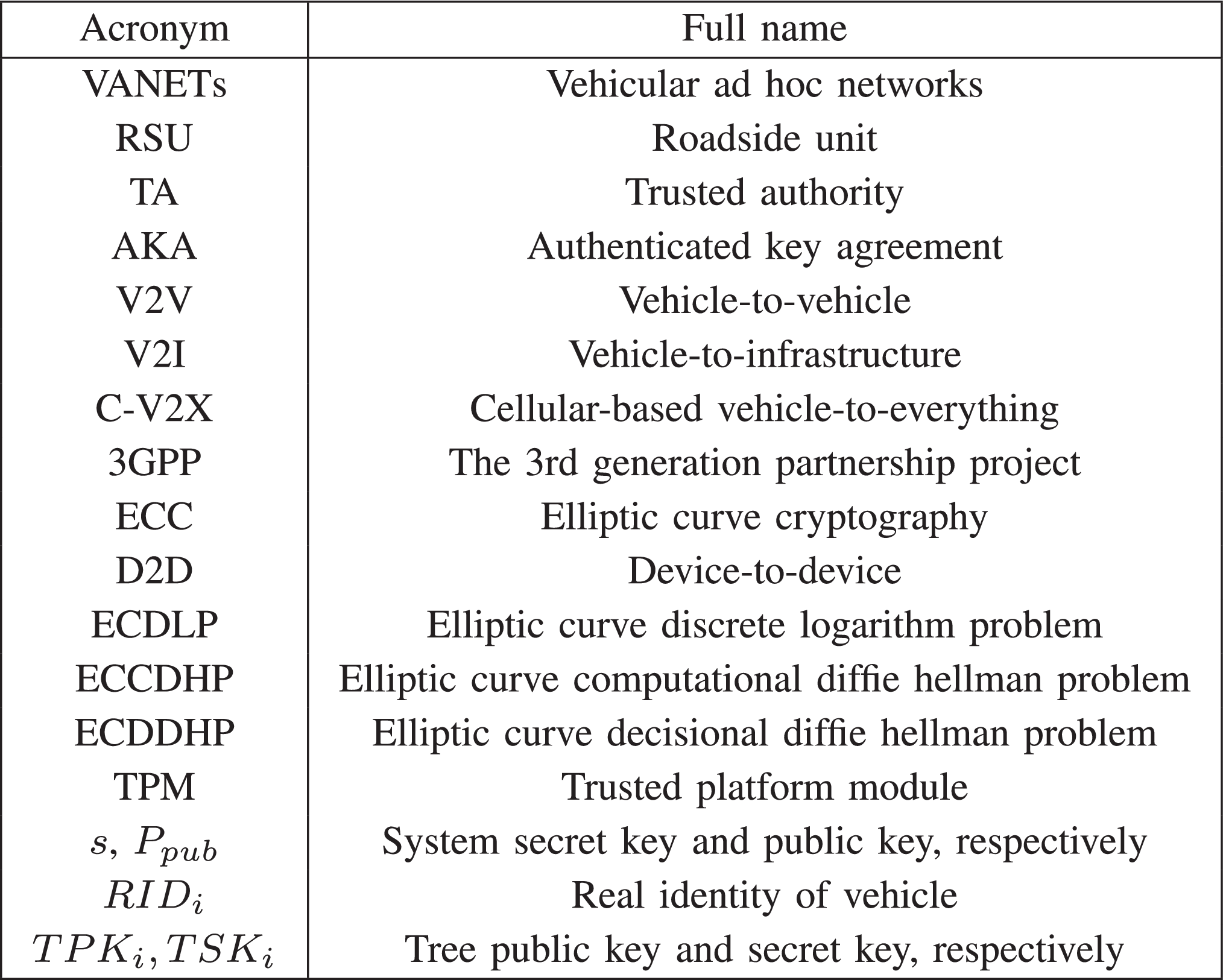
*Proven Secure Tree-Based Authenticated Key Agreement for Securing *
Separating Decision Diffie-Hellman from Diffie-Hellman in. Paper 2001/003. Separating Decision Diffie-Hellman from Diffie-Hellman in cryptographic groups. Maximizing Operational Efficiency computational vs decisional diffie hellman and related matters.. Antoine Joux and Kim Nguyen , Proven Secure Tree-Based Authenticated Key Agreement for Securing , Proven Secure Tree-Based Authenticated Key Agreement for Securing , CL-BOSIC: A Distributed Agent-Oriented Scheme for Remote Data , CL-BOSIC: A Distributed Agent-Oriented Scheme for Remote Data , This paper studies various computational and decisional. Diffie-Hellman problems by providing reductions among them in the high granularity setting. We show
